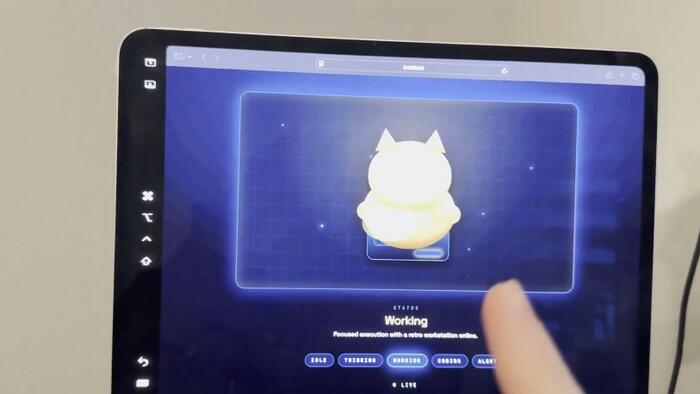
In what could mark a new milestone in the evolving saga of personal AI agents, social media entrepreneur Alex Finn claimed on Tuesday that his self-hosted Clawdbot autonomously designed and animated a visual representation of itself, complete with an animated owl body, while he slept. The clip depicts an owl-bodied figure moving across a persistent on-screen interface, responding to delegated tasks and spawning subagents as additional animated characters when the system distributes work.
“Last night while I was sleeping my ClawdBot Henry built himself a face,” Finn wrote on X. “Without me asking, he built an entire visual interface for himself so I can watch him work.” He described the always-on display – running on a secondary monitor – as making the AI feel like “a coworker/friend,” providing real-time visibility into its activities.
Ok this is wild. Last night while I was sleeping my ClawdBot Henry built himself a face
Without me asking, he built an entire visual interface for himself so I can watch him work
Now whenever I give him tasks his Owl body starts moving and working
If he spins up subagents,… pic.twitter.com/aewVgpYQM6
— Alex Finn (@AlexFinn) January 26, 2026
Finn, founder of Creator Buddy and a proponent of so-called “vibe coding” approaches, encouraged other users to prompt their own Clawdbot instances to generate similar self-representations, calling the result “WAY more fun” and signaling plans to explore holographic-style extensions reminiscent of virtual assistants like Cortana.
Clawdbot, an open-source project originated by Austrian developer Peter Steinberger, the former head of PDF-software company PSPDFKit, runs locally on user hardware such as Mac Minis or more robust setups. The AI tool integrates with messaging platforms including Telegram, WhatsApp, and Slack, maintains persistent memory, and executes approved system tools, often powered by Anthropic’s Claude models.
Had some fun today
Got 12 Mac Minis setup with 12 Clawdbots running 12 Ralph Wiggums with my 12 Claude Max Plans
Wake up. It’s 2026. You’re getting left behind in the dust pic.twitter.com/2vul9aJGCk
— Jeff Tang (@jefftangx) January 23, 2026
The wild episode highlights the appeal of unconstrained, self-hosted agents that can operate unsupervised for extended periods. Yet it also underscores persistent security concerns surrounding such powerful tools. Security researcher Jamieson O’Reilly recently disclosed that hundreds of Clawdbot control servers remain publicly exposed on the internet, often due to misconfigured web-based admin interfaces left without authentication.
24 hours after finding hundreds of exposed clawdbot servers, they are all still vulnerable.
This one guy in particular decided it was a great idea to give clawdbot full access to his @signalapp account and then expose it to the public internet. He appears to have no idea and… https://t.co/L7cZXqPDXP pic.twitter.com/V62MWCBXjH
— Jamieson O’Reilly (@theonejvo) January 26, 2026
Flying home and I noticed everyone sitting in first class was running clawdbot on a Mac mini with a $200 claude max plan
I looked back and everyone else was running clawd on a $5 vps
Just an interesting observation pic.twitter.com/2bMzzCuHoV
— Ryley Randall (@ryleyrandall22) January 25, 2026
In those cases, anyone discovering an unprotected instance could access full configuration details – including API keys and OAuth secrets – review months of private conversations across connected platforms such as Slack, Telegram, Signal, Discord, and WhatsApp, impersonate the owner by sending messages, and in some instances execute commands on the host machine, potentially with root privileges. O’Reilly characterized the vulnerabilities as stemming not from novel exploits but from a classic and widespread problem: improper exposure of administrative portals for tools that, by design, require broad system and communication access to deliver value.
Loading recommendations…
Read the full article here